MTConnect API Compliance Basics
Understand the essentials of MTConnect API compliance, focusing on security, integration, and standardization for modern manufacturing systems.
by Kevin Hood • May 12, 2025

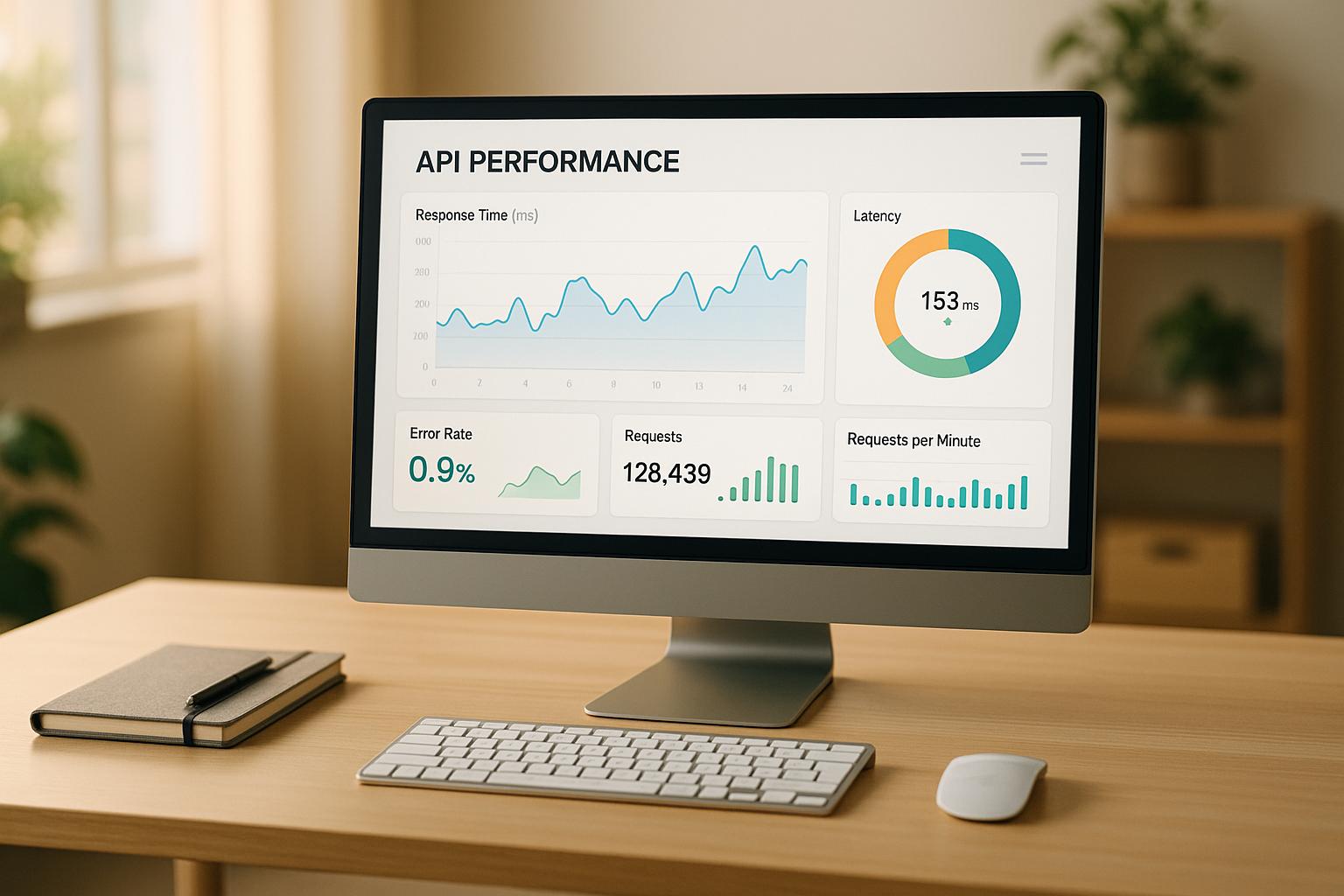
DreamFactory, API, API Latency, Throughput, Rate Limiting
Latency vs. Throughput in Distributed Rate Limiting
by Terence Bennett • May 9, 2025