
DevOps, DreamFactory, OAuth, SSO, API Security, GitHub, RBAC, JWT
How to Configure GitHub OAuth Authentication in DreamFactory: Complete Setup Guide
Enable passwordless SSO by integrating GitHub OAuth with DreamFactory, using RBAC and JWTs to securely control API access.
by Cody Lord • December 15, 2025

API Management, OAuth, API Security, documentation, Scope Naming
OAuth Scope Naming: 7 Best Practices
by Kevin McGahey • November 3, 2025

DreamFactory, OAuth, Low Code, erp, Healthcare, EHR Integration, Onprem
Top 5 Low-Code REST API Platforms for Secure Healthcare ERP & EHR Integration (2025 Guide)
by Kevin Hood • October 17, 2025

Facebook, Facebook OAuth 2.0, OAuth, Login, API
How to Incorporate Facebook OAuth 2.0
by Kevin McGahey • September 23, 2020
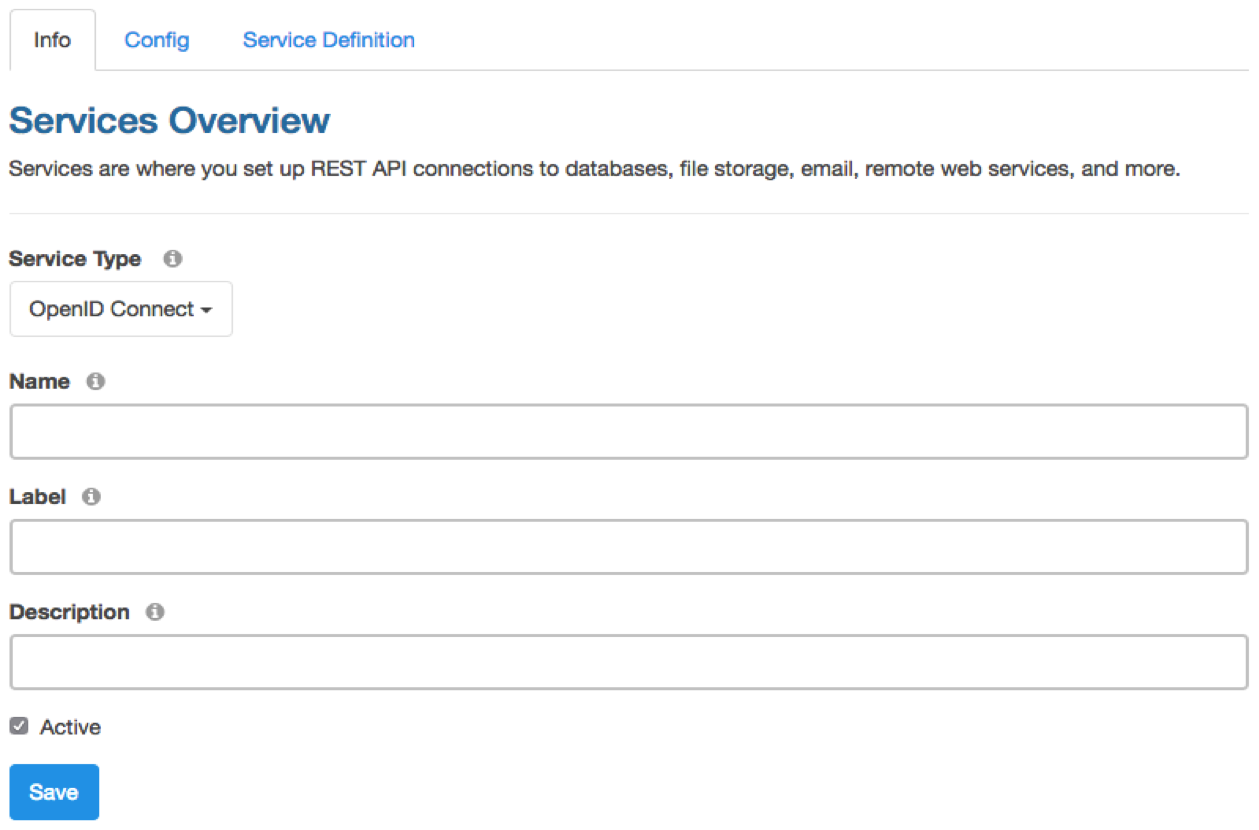
Services, User Authentication, OAuth, OpenID Connect, Authentication
Introducing DreamFactory's OpenID Connect Service
by Kevin McGahey • July 6, 2018
























