We get lots of inquiries about how the DreamFactory REST API platform helps secure data access, particularly from larger enterprise and government users. It's a valid concern: a growing number of web and mobile apps need to access sensitive data, and proper controls must be implemented in the services used to access that data from an expanding number of apps.
The good news for users is that securing data was one of our top design goals when architecting the DreamFactory platform. We can even argue that it can provide better data security than most custom-built APIs. But rather than arguing, I thought I'd just simply explain the inherently secure characteristics of the DreamFactory platform and the explicit security features that have been engineered into the plaform to help users securely mobilize data.
Native Install
DreamFactory is an open source software package that runs in the cloud or on premises. Single-click installers are available for most of the Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) cloud vendors. You can also run DreamFactory on a Linux, Windows, or Mac desktop computer. The software package includes a complete LAMP Stack with PHP and a dedicated SQL database that can be installed on any server.
These versatile installation options enhance security by putting organizations in control. They can use the same secure deployment practices for DreamFactory that they already use for their other applications. They can monitor usage, make backups, control cost, optimize performance, configure firewalls, and deploy applications with familiar tools and systems. Companies can choose a trusted cloud vendor or their own data center to manage application security.
Native installation and operation is a major advantage over Mobile Backend-as-a-Service (MBaaS) offerings. Since DreamFactory is not hosting the platform, there is no risk of our company losing your data. You do not need to worry about where our data center is located, who has access to your private information, or how we keep your data separate from other customer accounts.
Automatically Generated Services
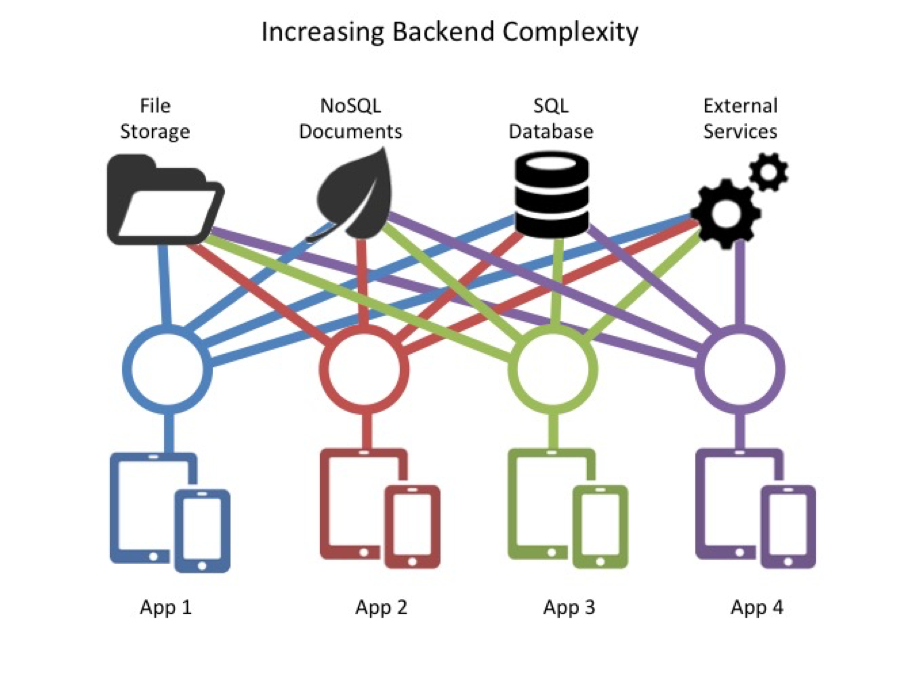
REST API complexity is a major security challenge. With each new mobile or web project, there is a tendency to create more and more project-specific REST APIs. Each service may be written in-house, by different developers, or by external consultants. These services typically have different user-management systems, different security protocols, different parameter styles, and different requests and responses. They will be hardwired to various data sources, and designed to run on different pieces of physical infrastructure. Over time, the server-side infrastructure can become increasingly complex, and each new REST API endpoint can potentially introduce new security vulnerabilities. And while API management and gateway products can help manage API endpoint access, they don't address the security and user permissions of the underlying services.
By contrast, DreamFactory automatically generates REST APIs and provides users with a unified REST API services platform, designed expressly with security in mind. This provides organizations with a single type of system for managing data access in a purpose-built REST API platform. The provides better security than trying to implement security features into an ever growing number of custom-built REST API endpoints.
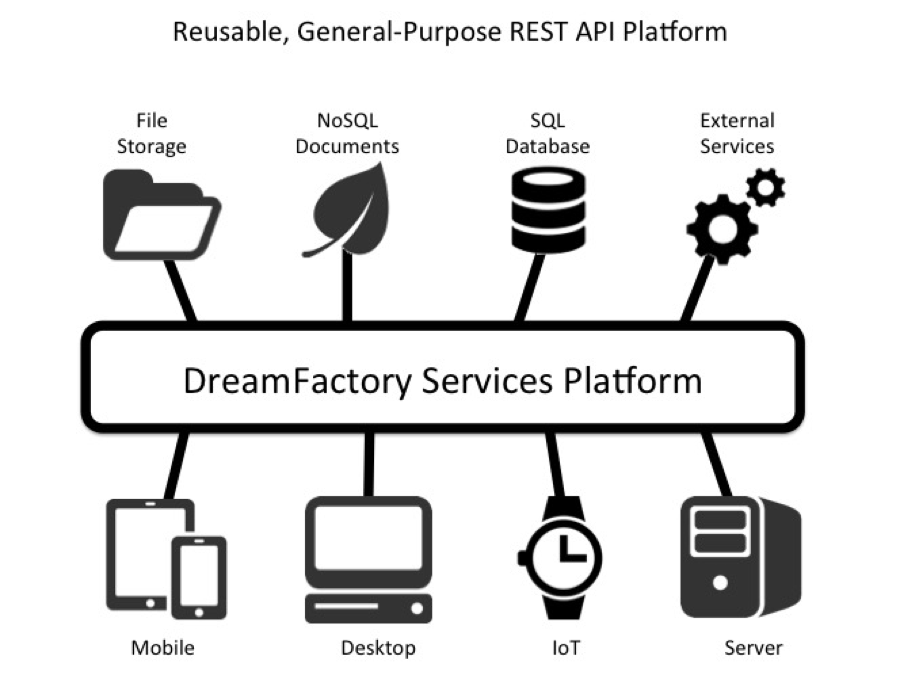
DreamFactory provides a comprehensive palette of secure, reusable, customizable REST API services. All of the various backend data sources are accessed through a unified REST API interface, providing a secure, RESTful services platform for general-purpose application development. The total number of exposed service endpoints is greatly reduced, and the connections and access controls to backend data sources are standardized and managed within a purpose-built system.
RESTful Services Platform
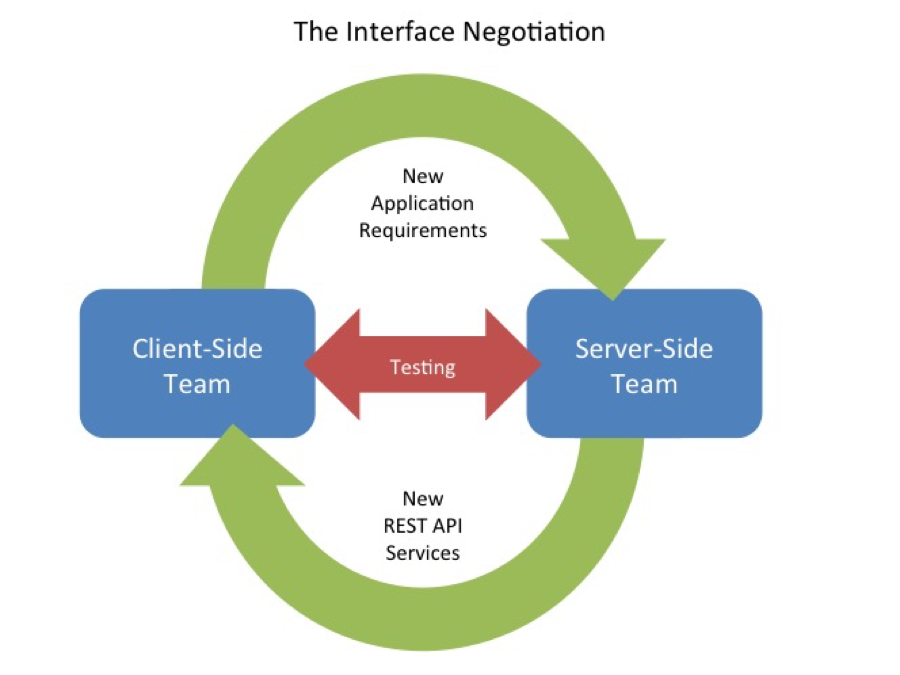
In a typical mobile development project, there is a client team and a server team, and the two groups must agree on a REST API interface. By auto-generating the needed REST APIs, DreamFactory stops this back and forth interface negotiation and allows each side to focus on their respective areas. DreamFactory enhances security by “decoupling” client-side application development from server-side user management and administration.
Services Abstraction
Applications written on a unified RESTful services platform also benefit from virtualization provided by the services layer. Services are no longer tied to specific pieces of backend infrastructure. Moving an application from development to testing and on to production is much easier. The services platform can be installed anywhere, so applications can be moved between the cloud and data center. Application staging becomes simpler, and overall application lifecycle management becomes more secure.
External Partners
In many projects, external consultants create the client-side application, and in some cases, they also build the server-side interface. With DreamFactory, trusted members of the IT staff can easily and instantly create secure REST APIs for each new mobile project. The platform can provide access to a staging or production database as needed. The client application can be moved from development, to testing, and on to production without code changes. This reduces the need to expose corporate information and backend systems to external partners working on development projects.
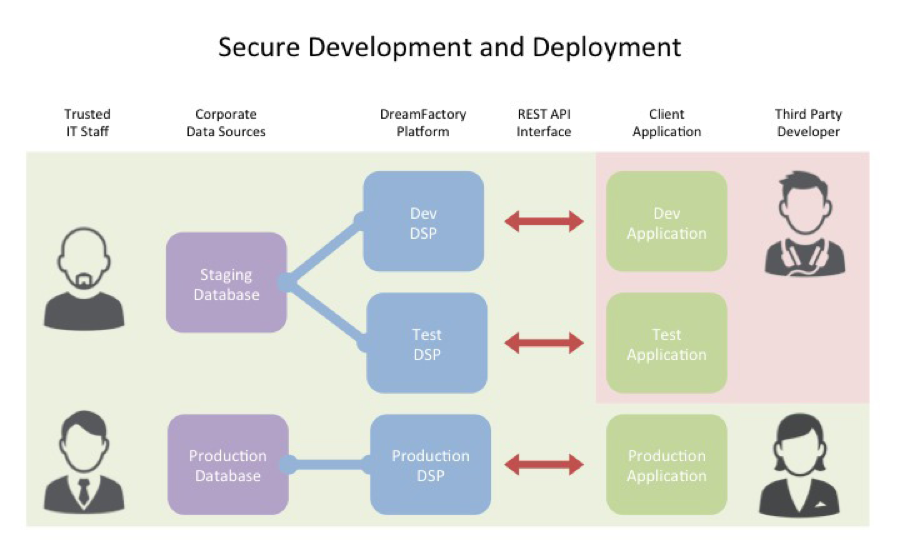
Single Sign-On
When a user signs on to DreamFactory they receive a session ID, which is securely managed as a browser cookie in an HTML5 application or as a transient local variable in a native application. All network transactions can be conducted over HTTPS, thus adding the security capabilities of SSL/TLS to standard HTTP communications.
Administrative updates to user roles and permissions are instantly reflected in the current session. For example, if a user is inactivated his session becomes invalid immediately. This provides a more secure environment for people entering or leaving the company, and for lost devices or security breaches.
Role-Based Access Controls
SQL databases have various tables, NoSQL databases have collections of documents, and File Storage Systems have different folders. DreamFactory users can define role-based access controls that govern which of these components are visible to a given user, along with HTTP verbs such as GET, POST, or DELETE that govern access.
Role-based access controls allow information to be hidden from certain groups. For example, individual salespeople might not have access to salary information, while this data might be available to managers. This capability prevents accidental data loss or disclosure of sensitive information. Roles also control which users can see which applications. This capability limits application access to unauthorized users.
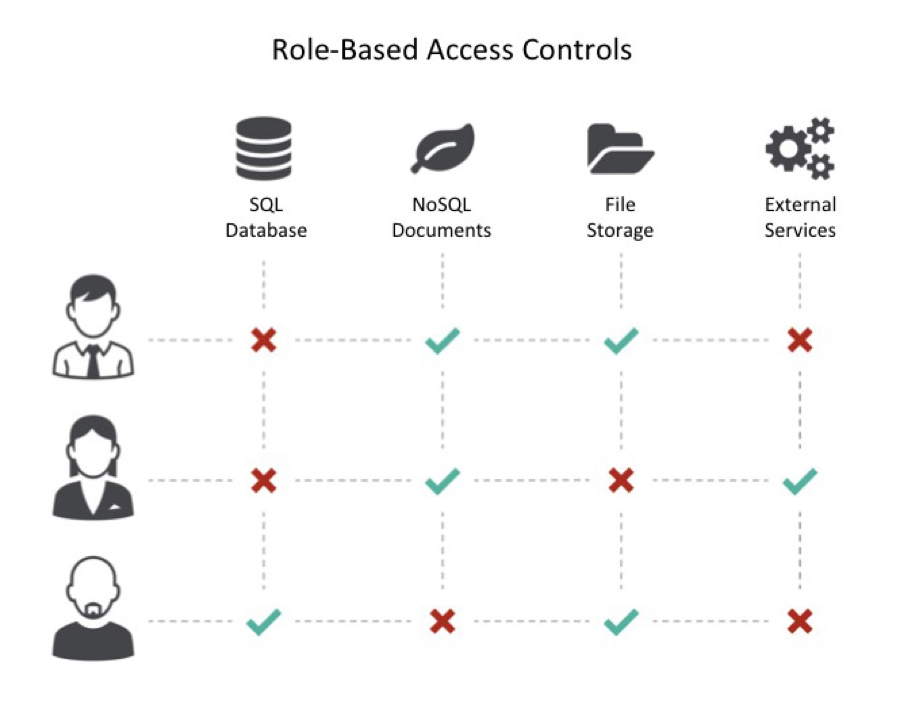
Record-Level Access Control
Roles can be customized with server-side filters to implement record-level access control. Each filter takes the form of a "field operator value" equation that must be true to enable access. The record-level access controls can impose constraints on external data sources. For example, you can limit data visibility only to records that the user created. This feature provides fine-grained security control of data sources.
User Management
DreamFactory provides very extensive user management features. Single sign-on, user roles, guest users, open registration, password resets, email services, email templates, and password hashing are all carefully implemented. The standardization of user management as a service and the integration of user management with the REST API platform prevent the security holes often found in custom API implementations.
Inheriting SQL Security
DreamFactory acts as a secure proxy for external data sources. When a SQL database is hooked up with a connection string, DreamFactory automatically inherits the security characteristics of that database. For example, if the connection string is for a read-only database user, then the REST API will deliver all the services as read-only, regardless of other access control settings.
DreamFactory can also inherit more complex permissions from a SQL database. You can configure server-side lookup keys to connect a user or role to the corresponding user or role on a remote database. This allows DreamFactory to mimic existing database security permissions, or change them as needed for mobile deployments.
Master Credential Storage
DreamFactory can connect to any number of external data sources and services. DreamFactory functions as a secure proxy that creates REST API services, provides server-side scripting, and enforces role-based access control. Each external data source or service will typically require a connection string, username, password, developer key, or some other type of master credential for access.
These master credentials are entered by an administrator in the DreamFactory Admin Console and encrypted for secure storage on the DreamFactory Services Platform. When an end user logs in through single sign-on, they have controlled access to external data sources and services as enabled by their user role, but there is no way for them to discover the master credentials.
This capability to hide master credentials securely on the DreamFactory server removes the need for client applications to use the master credentials for any external service. End-user access is provided through single sign-on and limited by the user-base access controls. Another benefit of this architecture is that external services can be activated, deactivated, or redirected without changing the client software.
Laravel Framework
DreamFactory is written with the latest version of PHP and the Laravel framework. PHP is the world’s most widely used server-side scripting language, and Laravel is the fastest growing framework for PHP. There is a very large community of professional developers using these products, and many mission critical websites depend on them for secure implementations. DreamFactory uses Laravel’s user management system and URL routing system for reliable and secure operation.
Programmable CORS access
DreamFactory implements Cross-Origin Resource Sharing (CORS) as a system level web service. The Admin Panel has a simple interface that can enable any host domain to use the DreamFactory REST API. By default, CORS is turned off and the services are only available from the originating host. Programmable CORS support prevents cross-site scripting attacks and use of the API from unauthorized sources.
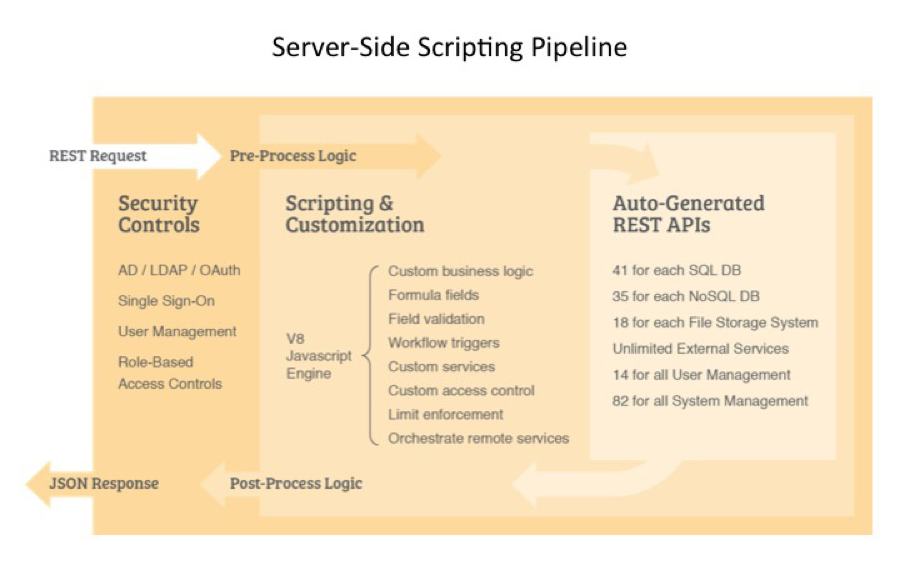
Server-Side Scripting
DreamFactory uses the V8 Engine developed by Google to run server-side code written in JavaScript. Any request or response can be examined, modified, or rejected by the scripting environment. This enables developers to customize any API call or develop new services as needed. The V8 engine is sandboxed, so server-side scripts cannot interfere with other platform operations.
Scripting and customization can be used for formula fields, field validations, workflow triggers, access control, custom services, and usage limits. A third party can use server-side scripts to safely customize the backend system. Custom security protections and notifications can also be implemented with server-side scripts.
Server-side scripts can use the REST API when needed. For example, a script might call the email service, trigger a push notification, or store some information in the database. The role-based access controls have separate settings that govern data access for both client-side applications and server-side scripts. This capability enables server-side scripts to safely perform special operations that are not available from the client-side REST API.
SQL Injection Attacks
The DreamFactory REST API for SQL includes the ability to use query filter strings as URL parameters. For example, you could request all of the Opportunities greater than a certain amount, or created before a particular date. Each query filter string typically has a field name, operator, and target value. They can be combined into complex expressions with parentheses and logical operators.
A SQL injection attack can occur when a hacker types a tricky text string into a search field or constructs a malformed query filter for use in a REST API call. They might use strange escape sequences, incorrect type handling, or unusual patterns of fields, operators, and values.
DreamFactory deconstructs each query filter string into individual name, operator, and value components. The field name must match the object, the operator must make sense, and the field value must be well formed. After this, the query filter string is reconstructed with only valid parameters. This prevents unauthorized SQL statements from being injected into the database.
URL Routing Attacks
Another attack vector concerns spoofed URL strings, illegal URL parameters, or tricky HTTP headers that somehow manage to bypass role-based access controls or otherwise returning sensitive data from the platform. DreamFactory uses the routing engine in the Laravel PHP framework to avoid this problem.
The security of the REST API interface has also been rigorously tested by hundreds of thousands of DreamFactory users actively building projects. The fact that all of the REST API calls have a single entry point is also more secure than having separate entry points for each backend system.
Open Source
The DreamFactory source code is available under the Apache License on GitHub. An open source product has "many eyes" on the code base. We have signed up for third-party security audits as well. DreamFactory Software also has quality assurance engineers looking for security problems on a regular basis. Thousands of independent developers are also testing the platform daily. The open source nature of the code base enhances security.
A Secure Ending
Most organizations only want authorized users to access sensitive data and API services must be secure--on multiple levels--to provide adequate security. As I mentioned at the top of this blog, DreamFactory was designed from the start to provide a highly-secure REST API services platform. I've summarized the many ways DreamFactory helps users securely mobilize their data. Perhaps I've even stimulated some thoughts (or concerns!) about security vulnernabilities in your current custom-built APIs.
Should you have additional questions on DreamFactory security features, the engineering team and I welcome your questions.
Terence Bennett, CEO of DreamFactory, has a wealth of experience in government IT systems and Google Cloud. His impressive background includes being a former U.S. Navy Intelligence Officer and a former member of Google's Red Team. Prior to becoming CEO, he served as COO at DreamFactory Software.
























 Blog
Blog